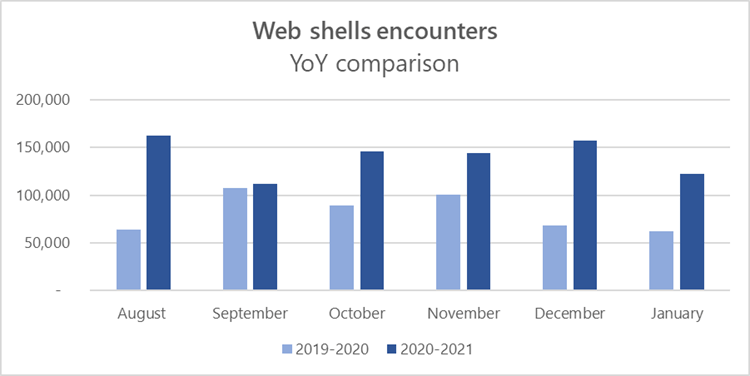
Between August 2020 and January 2021, there were 140,000 web shell attacks. (Microsoft)
How hackers can performing web shell
A web shell is a type of malicious code that can be uploaded to a web server, allowing an attacker to execute commands and scripts on the server. Hackers can use a web shell to perform various malicious activities, such as:
Gaining unauthorized access: A web shell allows an attacker to bypass authentication and execute arbitrary code on the server.
Data theft: Hackers can use a web shell to steal sensitive information, such as database credentials, stored on the server.
Server compromise: Web shells can be used to modify system files, install malware, or perform other actions that compromise the security of the server.
Remote command execution: A web shell allows an attacker to execute commands and scripts remotely, which can be used to launch further attacks or perform other malicious activities.
To perform a web shell attack, an attacker typically needs to find a vulnerability in a web application that allows them to upload a web shell to the server. This could be a result of poor coding practices, outdated software, or misconfigured permissions. Once the web shell has been uploaded, the attacker can access it using a web browser or other client and execute commands on the server.
It is important to secure web applications and servers to prevent web shell attacks. This includes regularly applying security patches and updates, properly configuring server permissions, and performing regular security audits to identify and address vulnerabilities
There are several methods that hackers can use to upload web shells to websites, including:
Exploiting vulnerabilities: One of the most common ways that hackers upload web shells is by exploiting vulnerabilities in web applications. For example, if a website is running an outdated or unpatched version of a content management system (CMS) such as WordPress, an attacker may be able to exploit a known vulnerability to upload a web shell.
Brute-forcing: Hackers can also attempt to gain access to a website by guessing the login credentials through a process known as brute-forcing. If they are successful, they can then upload a web shell to the website.
Social engineering: Another method that hackers use to upload web shells is social engineering. This could involve tricking an administrator into clicking on a malicious link or downloading a file that contains the web shell.
Cross-Site Scripting (XSS): XSS is a type of security vulnerability that allows an attacker to inject malicious code into a website. If a website is vulnerable to XSS, an attacker can use this vulnerability to upload a web shell.
Remote File Inclusion (RFI): RFI is another type of vulnerability that allows an attacker to include a remote file (such as a web shell) in a web page. If a website is vulnerable to RFI, an attacker can use this vulnerability to upload a web shell.
Once a web shell has been uploaded, the hacker can use it to execute arbitrary code on the server, steal sensitive information, and perform other malicious activities. It is important for website administrators to regularly check their websites for vulnerabilities and apply security patches to prevent web shell attacks
There are several known vulnerabilities that can be exploited to upload a web shell to a website, including:
Unvalidated Input: This is a type of vulnerability where user input is not properly validated, allowing an attacker to inject malicious code into a website.
File Upload Vulnerabilities: Some websites allow users to upload files, such as images or documents. If the website does not properly validate the uploaded files, an attacker could upload a web shell.
Cross-Site Scripting (XSS): XSS is a type of security vulnerability that allows an attacker to inject malicious code into a website. If a website is vulnerable to XSS, an attacker could use this vulnerability to upload a web shell.
Remote File Inclusion (RFI): RFI is another type of vulnerability that allows an attacker to include a remote file (such as a web shell) in a web page. If a website is vulnerable to RFI, an attacker could use this vulnerability to upload a web shell.
SQL Injection: This is a type of vulnerability where an attacker can inject malicious code into a website through a vulnerable SQL database.
Outdated Software: Websites that are running outdated or unpatched software may contain vulnerabilities that can be exploited to upload a web shell.
It is important to keep software up-to-date and to properly validate user input and uploaded files to prevent these types of vulnerabilities from being exploited. Regular security audits and penetration testing can also help identify and address vulnerabilities in a website
Hackers typically prepare for exploiting a web shell by researching and gathering information about the target website. This may involve performing reconnaissance and reconnaissance and vulnerability scanning to identify potential weaknesses in the website’s security.
Here are some steps that hackers may take in preparation for exploiting a web shell:
Information Gathering: The first step in preparing for a web shell attack is to gather information about the target website. This may involve researching the website, identifying the type of web server it is running, and determining what software and applications are being used.
Vulnerability Scanning: Hackers may use automated tools to scan the target website for vulnerabilities. This can help identify potential weaknesses in the website’s security that could be exploited to upload a web shell.
Exploit Development: Based on the information gathered and the vulnerabilities identified, the hacker may develop exploits that can be used to upload a web shell to the target website.
Test Environment: To avoid being detected, hackers may create a test environment to practice their attacks and ensure that their exploits are effective.
Attack Execution: Once the hacker is confident that their exploits are effective, they may execute the attack on the target website.
It is important for website administrators to regularly monitor their websites for signs of an attack and to implement security measures to prevent web shell attacks, such as keeping software up-to-date, properly validating user input and uploaded files, and regularly performing security audits.
Hackers often use a variety of tools to perform web shell attacks, including:
Vulnerability Scanning Tools: Hackers use vulnerability scanning tools to identify potential weaknesses in a target website’s security. Examples of these tools include Nessus, OpenVAS, and Acunetix.
Web Shell Upload Tools: There are tools available that make it easier for hackers to upload a web shell to a website. These tools often automate the process of exploiting a vulnerability and uploading the web shell.
Command and Control (C&C) Tools: Once a web shell has been uploaded, hackers use C&C tools to remotely control the shell and execute commands on the target server. Examples of these tools include Metasploit, Netcat, and reverse shell tools.
Remote Access Trojans (RATs): Hackers may use RATs to remotely access and control a target server. RATs can provide a hacker with a full range of control over the server, including the ability to upload and execute web shells.
Malware Analysis Tools: Hackers may use malware analysis tools to analyze and understand the behavior of web shells, which can help them evade detection and better understand how to exploit them.
It is important to note that these tools can also be used by security professionals to identify and prevent web shell attacks, so their use is not limited to hackers. It is also important to keep software and security tools up-to-date to ensure that vulnerabilities are patched and to prevent successful web shell attacks.
Website administrators can use a variety of tools to protect against web shell attacks, including:
Web Application Firewalls (WAFs): WAFs are security tools that are designed to protect websites from attacks. They can be used to block malicious traffic, such as web shell upload attempts, before they reach the target website.
Intrusion Detection Systems (IDSs): IDSs are security tools that are designed to detect and alert administrators to potential security incidents, such as web shell upload attempts.
File Integrity Monitoring (FIM) Tools: FIM tools are used to monitor changes to files on a website. If a web shell is uploaded, FIM tools can alert administrators to the change and allow them to quickly remove the web shell.
Anti-Virus/Anti-Malware Tools: Anti-virus/anti-malware tools can be used to detect and remove web shells and other types of malicious software.
Regular Backups: Regularly backing up website data can help administrators restore their website to a known good state in the event of a successful web shell attack.
Security Audits and Penetration Testing: Regular security audits and penetration testing can help administrators identify vulnerabilities in their website and ensure that their security measures are effective.
Keeping Software Up-to-Date: Keeping software up-to-date, including web servers, content management systems, and other applications, can help prevent successful web shell attacks by patching known vulnerabilities.
It is important for website administrators to implement a combination of these tools to protect against web shell attacks and to regularly monitor their websites for signs of an attack

